During WW2 German Enigma, then Lorenz messages were being decoded 50 miles north of London at Bletchley Park. You can visit the site to see how the Bombe machines, and the later Colossus computers cracked the Enigma and Lorenz codes. It’s very easy to get to from Euston Station.
Rotor based cipher machines started to appear in WWI and were invented simultaneously by different people. Arthur Scherbius patented a cipher machine in 1918 which he marketed under the brand name of Enigma. Originally they were aimed at commercial firms, including banks. The one below was bought by the British security services in 1926. I photographed it in the Bletchley Park visitor centre.

My top photo here is of the plugboard which the German army added to the front of Enigma machines. This took the chance of a message being decoded from a million to one against to trillions against. You can see why the Germans were very confident that their messages couldn’t be read.
During WW1 “Room 40”, in the Admiralty’s old building in Whitehall ran cryptanalysis for the British Admiralty. Later it’s functions merged with those of the army and in WW2 code-breaking was carried out at Bletchley Park. Bletchley Park was chosen because it was on the “Varsity Line”, the railway which once ran from Cambridge to Oxford. Two hundred scientists and mathematicians were brought in from each. It wasn’t until WW2 documents were declassified in the 1970s that Bletchley Park became famous. The people who had worked there kept silent about what they did in the war. Today GCHQ (Government Communications HQ) is based at Cheltenham, where it has been since 1951.
Visiting Bletchley Park
There are are variety of buildings at Bletchley Park that you can visit. They are all within walking distance of the station. There are lifts at the station and everything is wheelchair accessible. Bletchley Park, covers Enigma machine message reading huts, the Mansion itself, and special exhibitions. Full price admission is £20, but 50% off with the National Art Pass. You can revisit for free within a year. Your ticket also gets you into the National Radio Centre (photo below).

The National Museum of Computing is an extra £7.50 (£5 concessions) and houses a replica Bombe machine, a rebuilt Colossus II computer, plus many other things. To get to it go back outside the Visitor Centre, turn left, and it’s at the top of the car park. You get what you pay for – this is an amazing day out, and highly recommended.

Codes and Ciphers
Although the activities at Bletchley Park are often referred to as “codebreaking”, that is really a slang or colloquial term. Technically, a code is where a word or phase is substituted by a different word. One old commercial codebook substituted “Acerbity” for “Care of Brown, Shipley & Co., London.” This would make the message both faster and cheaper to send by morse code using a transatlantic cable. A cipher is where each letter is substituted by another. The German Enigma and their later Lorenz machines were cipher machines. For military use codes are not that secure as codebooks have to be distributed, and can be copied or stolen.
The use of encrypted messages goes back to the dawn of writing and were used by the ancient Greeks and Egyptians. Handwritten coded messages continued to be delivered by couriers on horseback until around 170 years ago when steam trains (and ships) speeded up the delivery times. Armies and Navies did use visual telegraph relay stations on ships and at the top of towers, but these were not secure. British ships were happily reading Napoleon’s signalling stations through telescopes.
Sir Francis Walsingham ran Queen Elizabeth I’s security service with amazing efficiency. His cryptologist, Thomas Phelippes, could read pretty much any message. Mary Queen of Scots incriminated herself in her own handwriting despite using about 100 different ciphers!
The first reliable transatlantic cable was put in place in 1866. It ran from Ireland to Newfoundland. Cables and cable laying rapidly improved, thanks to practical experience, and soon they spanned the globe.
In August 1914 Germany attacked France by sending troops though Belgium. They’d convinced themselves that Britain would not enter the war, despite existing treaties, and written warnings to the contrary. Within days of Britain declaring war on Germany a cable ship, Telconia, left Harwich and dredged up, cut and partly removed five German undersea cables. These had connected Germany to North and South America, Africa, and Spain. The use of wireless by the military had arrived. But anybody with a wireless receiver could listen in.
When the Titanic sank in 1912, survivors were only picked up because the ship was able to send out morse-code wireless distress signals, thanks to Mr Marconi. The technology had been proven.
Once the armies had dug themselves into trenches in WW1 they laid telephone lines and had no use of wireless. But the ships of the British and German navies came to depend upon wireless communication using morse-code. A message in morse code could cut through bad weather conditions and survive transmission with primitive equipment. From the start of WWI the British Admiralty was receiving transcripts of coded wireless messages that they could not read. A multi-talented team was setup in Room 40 in the Admiralty’s old building in Whitehall. Wireless interception stations were setup around the coast to listen in. Huge numbers of staff were employed to work for, rather than in, Room 40. They had a number of lucky breaks in 1914. The full set of three enemy code books were captured. The Admiralty was then able to read 2,000 encrypted German navy messages a day until the end of WWI.
Signals Intelligence
Thanks to the invention of wireless, Signals Intelligence, SIGINT, became hugely important.
Military leaders have always relied on intelligence to win battles. Biographies of great military commanders emphasise their superior tactics, weaponry, and bravery. What can’t be mentioned is the clandestine operations lurking in the background. They could never blow the cover of their agents, or reveal their methods.
Mistakes were made by both sides during the two World Wars. Initially neither side was as careful about communications as they should have been. Eventually the German navy began putting metal covers on their code books so that they’d sink if sailors on a captured ship threw them overboard. The top brass on both sides were initially dismissive of intelligence reports, until the inevitable defeats.

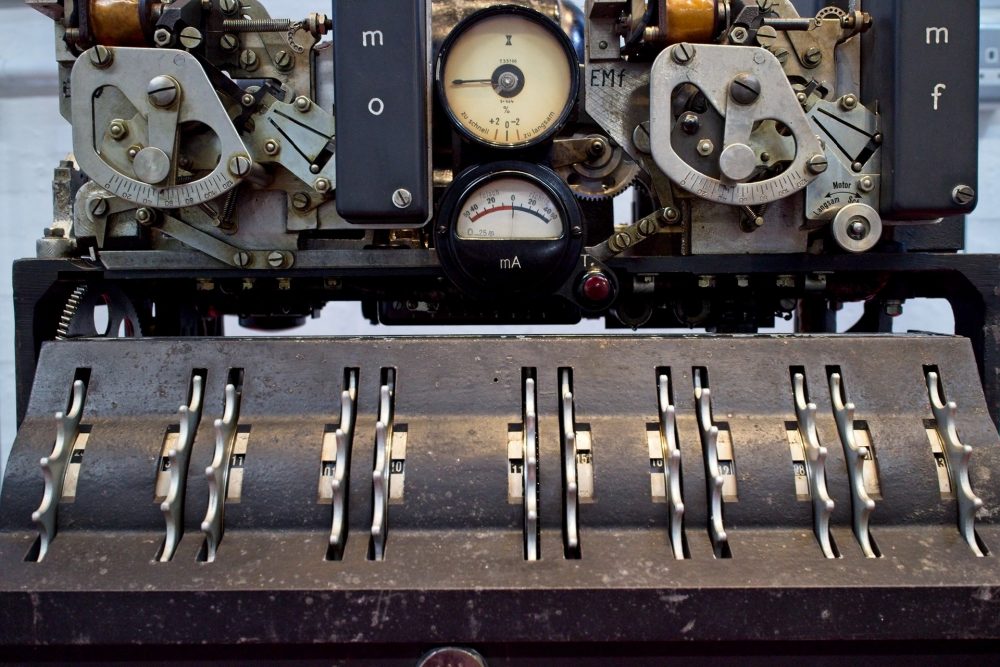
At the start of WW2 the German military were using 3-rotor Enigma machines with the plugboard. The great benefit of the Enigma was that it was portable, and could be used in the field. Since it was mechanical, it was less prone to to the errors made by an operator struggling with code and cipher books in rough conditions.
How Enigma machines worked
We had an excellent demonstration given to us of how the Enigma created it’s code in the National Museum of Computing, which is just outside the Bletchley Park fence. The machine setup changed every night and sheets detailing this were hand delivered by the SS each month. For the army machine you put in 3 rotors from a choice of 5, and dialled them to a start position. Then you setup the plugboard which switched the letters about even more. It needed two people to operate it. The operator held down one letter at a time from the message to be sent. Each time he pressed a letter down a different letter lit up on the flat top of the machine. An officer stood behind writing down the gobbledygook which was given to someone to transmit. The recipient also had an enigma machine setup the same way. He would type the coded message into his machine, one letter at a time, and the decoded message would be illuminated on the top.

Wireless Interception (Y-Stations), which were dotted around the British coast, wrote down the gobbledegook which was hand delivered to Bletchley Park by a fleet of female motorcycle couriers.
In 1937 British mathematician, Alan Turing, published a paper called “Computable Numbers”. He’d been theorising about a machine which could solve complex mathematical problems. He was thinking about true/false switching (binary code), and became interested in creating and cracking ciphers. It’s no surprise then that he should end up at Bletchley Park.
In the 1930s Polish engineers had managed to read code from fixed rotor Enigma messages. They’d used paper and card indexes. Following that they built a machine called a “Bomba” to try to read the coded messages faster. It wasn’t perfect. Then the Germans invaded and saw it. In response the Germans introduced interchangeable rotors.
The Bombe Machines
Alan Turing designed the first British Bombe machine which was running in March 1940. It sort of worked. Gordon Welchman modified the circuitry and from Aug 1940 50x faster Bombe machines were reading 1,000 Luftwaffe messages a day, right to the end of the war. The curator in the museum told us that each machine cost the same as a Wellington Bomber. By the end of the war 211 had been built, including newer models to read 4-rotor Enigma traffic. The machines are about 7 feet square and weigh one ton.

The was a notice beside the Bombe machine above giving the time of the next demonstration. We went back to see it run and hear how it worked. As you can see the machine had vertical sets of 3 drums – 3 rows of twelve. There were thousands of wires round the back and the drums spun at speed. It was designed operate like a reverse Enigma Machine. I’m simplifying here – using intuition, and whatever else was to hand, the codebreakers at Bletchley guessed a word which might be in a message. They ran the Bombe machine that worked though all the possible coded combinations until it came up with a match in the original message. If they were lucky they might establish that day’s enigma code in half an hour.
Throughout the war any military usage of intelligence from Bletchley Park had to have a cover story showing how they could have got the information by other means. For example: on 25th May 1941 Enigma messages were received saying that Germany’s most feared battle ship, Bismarck, was heading towards Brest for repairs in the night. A Catalina flying boat just happened to fly overhead and see her. The Bismarck was finally sunk a few days later. It was essential that the Germans continued to believe that their ciphers were unbreakable.
In Feb 1942 the German Navy introduced a new M4 Enigma machine with an extra rotor. It came with a code book to shorten messages speeding up transmission times and to confuse anybody listening in. Admiral Karl Dönitz, who commanded the U-Boat fleet, was a wily man. All his Enigma machines had a choice of 8-rotors. He also started addressing his boats by the captain’s name rather than ship’s. It took Bletchley Park 9 months before they could read German Navy messages again. From around the end of 1943 the effectiveness of the U-Boat blockade declined. Dönitz was horrified to find his intercepts of British messages included the names and locations of his U-Boats. He suspected his Enigma messages were being read again, they were, but there was something else. The British had developed short wave radar and could see the U-Boats.
Reading Lorenz ciphers with the Colossus computers
In mid 1942 the German high command was using a small number Lorenz cypher machines which had twelve rotors. These were much faster than the laborious Enigma machines. They had a typewriter style of keyboard and produced longer encrypted messages on a paper tape. The tape could be joined to other messages and transmitted at speed by a teletype machine. This transmitted a radioteletype code linking one machine to another by wireless, instead of a telephone cable. Y-Stations were reporting “new-music”.
Max Newman worked out how to read the “Tunny” code produced by the Lorenz teletype machines. It took so long that it was of no military use, but he had proved that it could be done. What was needed was some kind of faster codebreaking machine.

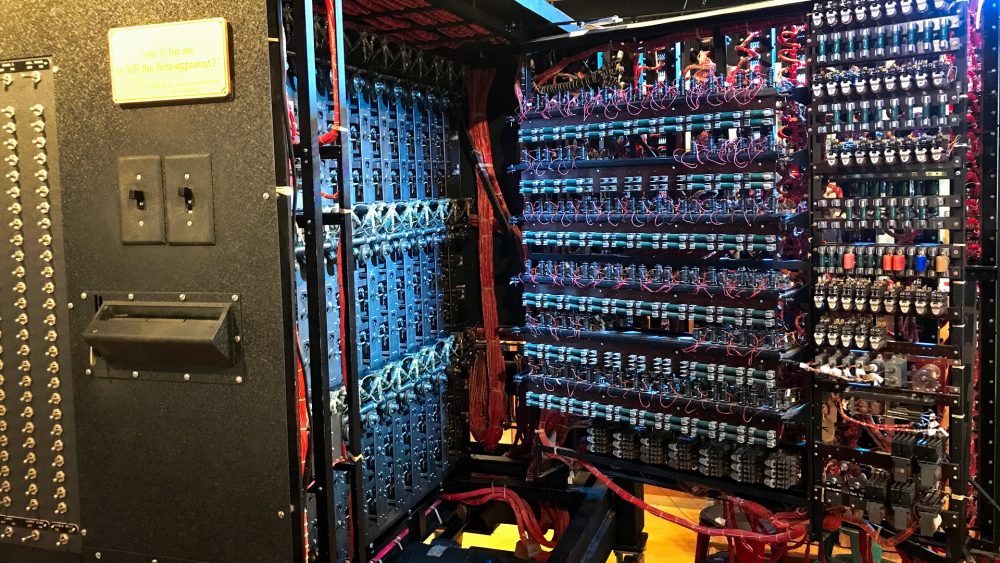
In 1943 Turing was reading up about electronic circuits and brought Charles Wynn-Williams in. He said it was possible to build a circuit using valves which could switch 1,000 times faster than relays. Turing had already encountered Tommy Flowers at the Post Office Research Station at Dollis Hill and asked him for help. Flowers and Frank Morrell built a machine that they actually called the Heath Robinson. It was prone to breaking down and catching fire. Flowers suggested building a machine with 1,600 thermionic valves in it, which was named Colossus. It was up and running in Bletchley Park in January 1944. The Colossus MKII which I photographed here swiftly followed. It was 4x faster, with 2,400 valves. The room was a bit hot.
The British were soon punching their own copies of the encrypted paper tape. It was run in an endless loop through a reader linked to the the Colossus. It kept reading the teletype tape at 5,000 characters a second until it had cracked the message. Ten Colossus computers were built. From then to the end of the war pretty much all the German high command messages were being read.
By the end of WW2 9,500 people were working for Bletchley Park at a number of locations. The Bombe machines and Colossus computers were also spread around the country. Our investment in people and resources for Signals Intelligence was many times more than the Germans, which is why we more more successful.

After the war nobody who worked at Bletchley Park could speak about what they did because of the Official Secrets Act. Then the Cold War started, so restrictions couldn’t be lifted. Friends and relatives of people who worked there thought they’d spent a cushy war doing office work. Tommy Flowers was refused a bank loan to build a commercial computer, because they said it would be impossible to do. He couldn’t say that he’d already done it. Tommy Flowers was born at 160 Abbott Road, Poplar. He’s commemorated on the Aberfeldy Estate.
A week before Sheila and I went I got a couple of books out of the library to swat up on Bletchley Park. It was useful – there’s a lot to learn! The staff and curators we encountered were all very knowledgeable and helpful.
We had a fantastic day out a Bletchley Park, and a great lunch in Hut 4, beside the main house. You can visit Bletchley Park on a Birmingham bound train from Euston. The return tickets cost us £13.35 each with a railcard. There’s about four trains an hour and takes 35-50 minuted depending on the number of stops. Book West Midlands Trains here.
Alan Tucker


